25.10
Describe five factors that engineers should take into account during the process of building a release of a large software system.
-
Competition:
A new system release may be necessary because a competing software product has introduced new features, and existing customers may choose the competing product if those new features are not provided to them.
-
Marketing requirements:
The marketing department may have promised new releases on a particular timeline, or it may be necessary to include new features in a system to persuade users to upgrade from an outdated release.
-
Platform changes:
A new release of your software may be required if the software it runs and depends on (such as an operating system) has a new release.
-
Technical quality of the system:
Serious system faults that affect numerous users may need to be corrected in a release. Minor faults, however, can be repaired in patches that can be applied to the current release.
-
Documentation:
Thorough documentation must be provided in each release so that in the event of an issue with any release, you have the ability to recover every component used in that release.
21.4
Explain why program inspections are an effective technique for discovering errors in a program. What types of error are unlikely to be discovered through inspections?
Program inspections are extremely effective because they allow a developer who wasn’t involved in writing the program to look at it. I’ve personally had numerous code errors discovered by formal and informal code inspections. Most of the time, program inspections catch errors that I overlook after looking at the same program for a long time such as simple syntax errors, incorrect logic, etc. Formal program inspections, such as reviewing pull requests on GitHub, tend to reveal more nuanced errors such as web page styling that doesn’t meet the program’s requirements.
Despite being an effective technique for discovering errors, program inspections do not usually reveal runtime errors. Sometimes it's easy to spot what might happen at runtime, but not all runtime errors are easy to see. It's not until the program is actually run that runtime errors might become visible.
My team, Don’t Test Me, has made excellent progress on our team project. We have essentially finished our csore project. We have implemented 25 passing test cases for five different model methods in Canvas, and the test cases are displayed in an HTML page. This past deliverable was fairly straightforward since we implemented a test superclass called Testatron. In fact, I was able to implement a set of five test cases in less than 10 minutes. I am extremely happy that we were able to design our test suite in a way that made it easier for everyone on the team to implement future test cases. This also means that our test suite should be easy for others to build on in the future if the want.
I’m also extremely pleased that everyone on my team has made an effort to properly build this project and has committed themselves to meeting each deadline on our timeline. I have no doubt that our last few deliverables will run just as smoothly!
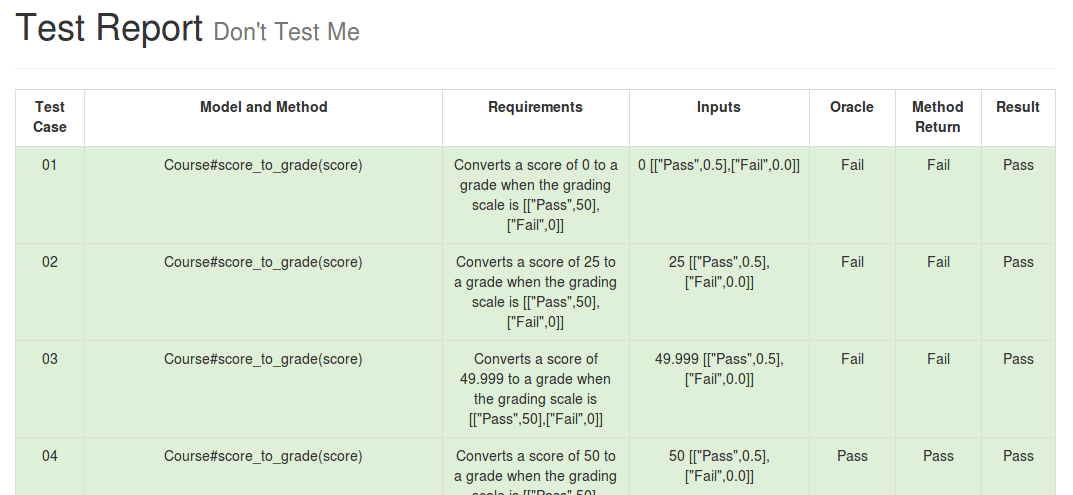 A screenshot of our test suite
A screenshot of our test suite
23.6
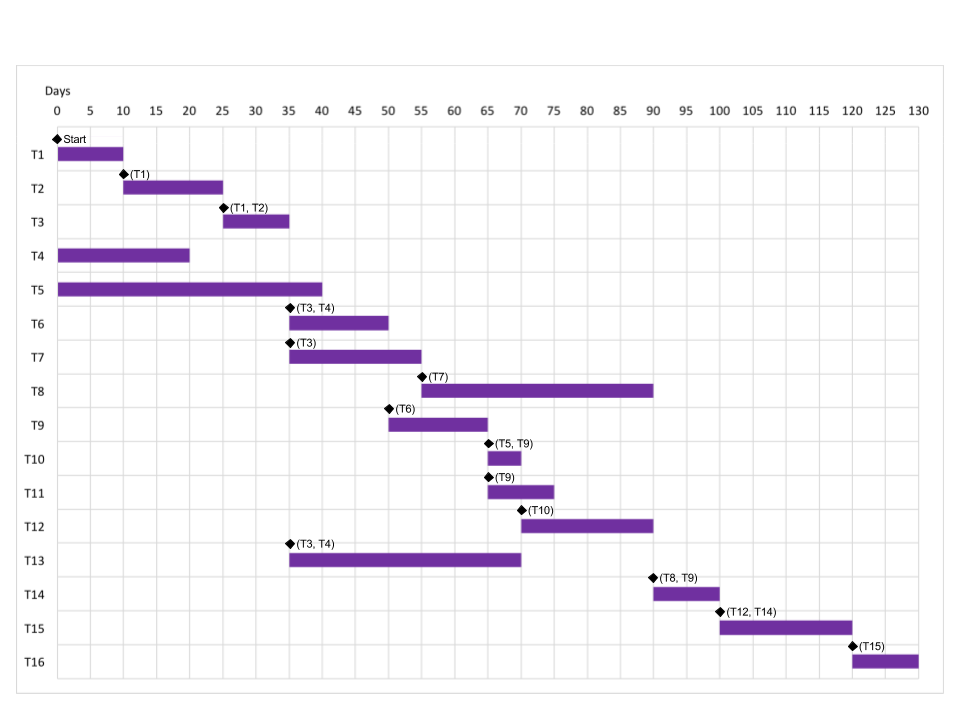
Figure 23.14 shows the task durations for software product activities. Assume that a serious, unanticipated setback occurs, and instead of taking 10 days, task T5 takes up to 40 days. Draw up new bar chart showing how the project might be reorganized.
22.6
Fixed-price contracts, where the contractor bids a fixed price to complete a system development, may be used to move project risk from client to contractor. If anything goes wrong, the contractor has to pay. Suggest how the use of such contracts may increase the likelihood that product risks will arise.
A blog post from Salsita Software, a professional software consulting company, nicely summarizes the issue with fixed-price contracts: “accurate software estimation is not possible even when perfect information is available about project requirements.” Software is intangible, complex, and generally differs from project to project, making it extremely difficult to accurately estimate a timeline and budget at the beginning of a project. If the contractor’s estimates end up being too optimistic, then the contractor might have to take a loss in pay, the developers might have to work overtime, and bad code may be produced as a result of a rushed schedule or tight budget. In this case, the risk of missed deadlines, blown budgets, and developer turnover increase. Additionally, if poor quality software is produced, which is likely, then the contractor risks their reputation, which can lead to fewer projects in the future. If the contractor plays it safe and estimates the project to cost much more money and take much longer to produce than it actually took, then the customer pays more than a fair amount for the work actually done. In this case, quality code may be produced, but the customer may not be happy that they overpaid for the contractor’s services, again risking the contractor’s reputation.
A better way to manage a software project is to have open and frequent communication between the client and contractor, and follow Agile methodologies when appropriate. This approach supports unforeseen changes in a software project, and allows the contractor and client to easily communicate changing requirements, costs, and timelines.
21.4
Explain why an object-oriented approach to software development may not be suitable for real-time systems
Real-time systems have strict timing constraints. Object-oriented development is centered around hiding data and reading or modifying that data using getter and setter methods. Using getter and setter methods, however, can result in a loss of performance, which may make meeting those strict timing constraints impossible.
Additionally, real-time systems are process-oriented, not object- or component-oriented. Process-oriented systems focus more on efficiently sending data between hardware. Object-oriented development do not accurately represent the underlying architecture of process-oriented systems.
So far, our project has met all of the deliverable deadlines with ease. My team has been fantastic about working together remotely over Slack and making use of the time we have together in class to work on this project. At the beginning of this semester, none of us had any experience with Bash scripting, and only Kyle and I had any experience with Ruby on Rails applications. At this point in the project, all of us are familiar with Canvas and writing simple Bash scripts. Overall, our experiences with this project were not as difficult as expected, however, we overcame a few notable obstacles.
First, we had some difficulties installing our chosen H/FOSS project, Canvas LMS. We found that the all-in-one installation script provided in the Canvas repository was outdated and failed before it finished installing. This wasn’t too much of an issue for us because we wanted to set up the application manually at least once regardless of the all-in-one script. The biggest issue with installing Canvas was installing the required dependencies, particularly, a customized jQuery gem. Canvas uses a custom fork of jQuery 1.7.2 with a minute change. When Canvas’s asset management tool, Yarn, tried to retrieve the code from that jQuery repository, it complained about an Invalid Tar Header coming from the source of the repository. Unable to get the custom jQuery to install, we tried installing various other versions of jQuery. Eventually, we found that jQuery version 2.2.4 installed and allowed us to start a local Canvas server. Everything seemed fine until the homepage loaded, and the page seemed oddly sparse. We continued to struggle with jQuery for a while before finally deciding to submit an issue on Canvas’s GitHub page. While writing the issue, we decided to reset the jQuery version used by Yarn to get a screenshot of the issue, but that seemed to fix our problem. We’re still not entirely sure what fixed the issue we were having, but we included some steps and asset files that were only mentioned in Canvas’s Production Start Guide that seemed to fix our problem.
Our next biggest obstacle was finding a way to run specific model methods without access to the entire Canvas code base or a testing database. In Ruby on Rails, all model classes extend Active Record, a class that maps object instances to a relational database so that they can be persisted. This isn’t an issue for writing unit tests in RSpec, but it made it difficult to write unit tests that are external to Canvas. After some research, we found a gem called activerecord-tableless which allows us to essentially bypass Active Record. Once we were able to install this gem, writing and running tests became fairly simple.
At this point, I am highly satisfied with the effort that my teammates and I have put into our project. We have all advanced our knowledge of testing practices and scripting. Additionally, everyone has gone above and beyond to ensure this project succeeds and meets deadlines.
If you would like to see more about our team project, visit our team repository here.
20.10
You work for a software company that has developed a system that provides information about consumers and that is used within a SoS by a number of other retail businesses. They pay you for services used. Discuss the ethics of changing the system interfaces without notice to coerce users into paying higher charges. Consider this question from the point of view of the company's employees, customers, and shareholders.
This is a terrible idea. I believe that a company should never take advantage of its users, especially if those users have no way to protest the change until after it’s implemented. Changing an interface and charging more for it can interrupt the plans and budgets of the users who use it. From a shareholder perspective, this can mean that new and existing customers can’t trust the company to be reliable. While this decision might bring in more revenue in the short run, in the long run it is likely to hurt profits because it damages the user’s trust. Aside from financial decisions, I would not be comfortable with this business plan as an employee. It simply seems wrong. I wouldn’t want a company to change their interfaces just to charge me more, and I wouldn’t want to do that to my system’s users either.
18.4
Why is it impossible to infer the emergent properties of a complex system from the properties of the system components?
It is impossible to determine the emergent properties of a complex system from its components because emergent properties can only be distinguished after the system components are integrated. Emergent properties of a complex system are highly dependent on how its system components interact, which isn’t possible to entirely determine in a complex system by examining the components individually.
18.4
Define an interface specification for the Currency Converter and Check credit rating services services shown in Figure 18.7.
Currency Converter service interface specification:
| Operation |
Inputs |
Outputs |
Exceptions |
| ConvertCurrency |
ccIn
initial currency type
converted currency type
amount to convert
|
ccOut
converted currency type
converted currency amount
|
ccFault
invalid initial currency type
invalid converted currency type
invalid amount to convert
|
| LookUpFee |
lookfeeIn
initial currency type
converted currency type
|
lookfeeOut
percent fee on currency exchange
|
lookfeeFault
invalid initial currency type
invalid converted currency type
|
| LookUpExchange |
lookexIn
initial currency type
converted currency type
|
lookexOut
exchange rate between currencies
|
lookexFault
invalid initial currency type
invalid converted currency type
|
Credit check rating service interface specification:
| Operation |
Inputs |
Outputs |
Exceptions |
| GetCreditRating |
gcrIn
social security number
name
date of birth
|
gcrOut
credit rating
|
gcrFault
invalid ssn, name, date of birth
no credit rating found
|
17.10
Your company wishes to move from using desktop applications to accessing the same functionality remotely as services. Identify three risks that might arise and suggest how these risks may be reduced.
- Transparency: Ideally, the remote services should not be affected due to the way they are remotely distributed. The remote services can appear more like a single system by using Middleware to map resources referenced by a program to remote physical resources.
- Quality of Service: In order to reduce the risk of a distributed system providing poor quality services, the Quality of Service requirements should be defined in advance. This is especially important if the system deals with audio streams, video streams, or other critical data. Once the Quality of Service requirements are defined, it can be determined whether or not those requirements can be met given the available resources.
- Security: This is a major issue in distributed systems because often the components of a distributed system are managed by separate organizations with mutually incompatible security mechanisms. Whenever possible, each component of a distributed system should be secure so that it can’t be compromised via some other compromised component.
16.9
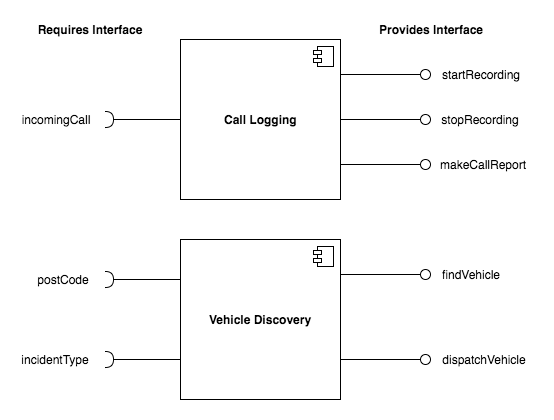
Design the interfaces of components that might be used in a system for an emergency control room. You should design interfaces for a call-logging component that records calls made, and a vehicle discovery component that, given a post code (zip code) and an incident type, finds the nearest suitable vehicle to be dispatched to the incident.
9.8
Briefly describe the three main types of software maintenance. Why is it sometimes difficult to distinguish between them?
The three types of software maintenance are:
- Fault repairs to fix bugs and vulnerabilities (corrective maintenance)
- Environmental adaptation to adapt to the software to new platforms and environments (adaptive maintenance)
- Functionality addition to add new features and to support new requirements (perfective maintenance)
Sometimes it’s hard to distinguish each type of software maintenance because they overlap one another. For instance, new features may be might be added to a system when the software environment is updated, or an environment may be upgraded to easily fix a bug, and so on.
9.10
Do software engineers have a professional responsibility to develop code that can be easily maintained even if their employer does not explicitly request it?
Of course software engineers should develop code that can easily maintain, regardless of whether or not it was explicitly requested. At the beginning of this course, we were required to read the ACM Software Engineering Code of Ethics and Professional Practice. In the code of ethics, it states that software engineers should develop software in the best interests of the public, their employers, clients, and colleagues. To make software less costly to maintain, and make the lives of fellow software engineers and developers easier, software should be developed with maintainability in mind. Additionally, the code of ethics specifically states that “software engineering managers and leaders shall subscribe to and promote an ethical approach to the management of software development and maintenance.” Therefore, software engineers must develop code that can be easily maintained in order to adhere to the ACM Software Engineering Code of Ethics.
15.10
The reuse of software raises a number of copyright and intellectual property issues. If a customer pays the software contractor to develop a system, who has the right to reuse the developed code? Does the software contractor have the right to use that code as a basis for a generic component? What payment mechanisms might be used to reimburse providers of reusable components? Discuss these issues and other ethical issues associated with the reuse of software.
To me, the simplest solution to determining who has the right to reuse developed is to let the developer decide who can reuse the code they developed. Each time we sign up for a new account on a website, every time we install a new application, and nearly any time we use any service, we agree to a set of rules for using that software or service, often called the Terms of Service or a Licensing Agreement. If the developers of the software want other developers to be able to reuse and edit their code, such as the developer of Linux, then they can specify that in their terms of use. If the developers want their software to not be reused by anyone outside of their team or company, or not even to be run on any hardware, such as Apple’s OS X, then they can specify that in their terms of use. Any number of rules and conditions can, and should, be specified by the developers of a software system.
Not every software system should be open to external extension and reuse, especially to outside developers, regardless of how much time and money could be saved. Of course, the original team of developers should at least revisit previous conceptual solutions to a system before creating a new system to solve the same problems, even if they plan on rewriting them instead of reusing them. However, not all code should be open to just any outside developers. For example, banking apps. Wells Fargo is free to reuse their own software at their discretion for a new banking app, but security issues could arise if their apps were open-source. Therefore, I believe they should have tighter control over who can reuse their mobile banking app software. Additionally, not all software should be reused without considering implications of reusing that software. The Therac-25 radiation therapy machine reused software from a previous model, but its creators didn’t consider possibility of the old software failing, and decided to forgo installing hardware safety checks. Because of this, I believe that software reuse should save time and money on development costs, but not in testing costs. Since behavior can change when a software system, or a portion of a system is reused, the new system needs to be analyzed and tested as thoroughly as an entirely new system.
HW14: Testing Reflections
It made me smile that Boris Beizer noted that nobody likes testing in the first few sentences of the Introduction in Software Testing Techniques. I personally dislike testing, despite knowing its necessity. In The Mythical Man Month, Brooks states that we love to program because we love making things, we love making useful things, we like solving complex problems, etc. Testing is none of those things. They may be useful, but they’re not something that people often interact with, so they’re not useful in a way that brings us much pleasure. With anything else I don’t enjoy doing, it helps to have motivation to do it, and Beizer offers a compelling argument on why testing is important.
Something I found really interesting about this introduction was the benefits and pitfalls of being a tester with knowledge of the system design. Testers with no knowledge of the software's design and intended use are more likely to break it by creating unusual, unintended test cases, which could be useful or unnecessary. The more a tester knows about the software’s design, the more efficiently you could test the software, but the tester may not think about odd use cases that would reveal a bug in the code. Beizer suggests that there should be a balance between the unintelligent testing mentality and the software designer mentality, and the separation between those two may differ depending on the project. This is something I personally need to keep in mind at my internship. My development team consists of only eight developers and one lead architect, and we are responsible for writing all of our unit tests and some systems tests. In my team, each developer is part software designer who implements a solution to a given problem, and part tester who is responsible for testing the solutions we provide.
Ultimately, we test to create low-risk software. Ideally, we implement our software in a way that is easy to test, resulting in less effort dedicated to writing tests and code with fewer bugs. That’s great, and something we should strive for, but the most frustrating thing Beizer points out about testing is that it’s impossible to prove that a system is bug-free. It’s always nice to see that all of my automated tests are passing, but it’s upsetting to think that no matter how much I test, I can never prove that my system is bug-free. To me, this makes testing even less satisfying. You can only try to determine how much testing is “enough.”
8.7
Write a scenario that could be used to help design tests for the wilderness weather station system.
Ashton uses the wilderness weather station system in the remote town of Fort Severn, ON, Canada to gather and report weather information. Every morning around 6am, Ashton requests a weather summary report.
When the local weather station system is able to connect to the remote data management system via satellite communications, the local weather station system notifies Ashton that her request for a report has successfully been sent. Once the report has been completely transmitted to Ashton’s local weather station system, the report is displayed.
Ashton knows that it often snows in northern Ontario, making it impossible to establish a stable connection with the satellite communication systems. If satellite communications are unavailable or interrupted due to poor weather conditions, the report is unable to be transmitted to Ashton’s local weather station system, and the system notifies her that it is unable to connect to the remote data management and archiving system. This isn’t a big deal to Ashton. She understands that the conditions in such a remote location can be harsh, and that her local weather station system will continue to establish a connection to the satellite communications systems for 24 hours before giving up. Once it is able to establish a connection and receive the weather summary report, Ashton is notified.
8.10
A common approach to system testing is to test the system until the testing budget is exhausted and then deliver the system to the customers. Discuss the ethics of this approach for systems that are delivered to external customers.
Depending on the size of the testing budget, the amount of time dedicated to testing the software, and how the developers approached testing the system, this approach could work out nicely or end disastrously. Since this approach can lead to a wide range of results, it’s not the best approach to systems testing, and is a generally unethical approach. This is especially true in safety-critical systems such as airplane navigation software or human vitals monitoring systems used in hospitals.
A more ethical approach to system testing is to devote at least half of the estimated schedule to testing, as noted by Fred Brooks in the Mythical Man Month. Budgets can quickly be exhausted if numerous flaws are detected in the system during testing, which is an important aspect of testing a system. If it happens that a particular system’s testing budget is quickly used up but not every use case was accounted for in tests, it’s likely that there are more unknown flaws delivered to external customers than there would be if all use cases were tested.
I found chapters 1-4 of The Mythical Man Month to be quite interesting, not entirely because I learned numerous new concepts (I did learn a few things), but because Brooks explained in detail several things I learned to be true about software engineering and project management through my own experiences. For instance, the central theme of the book is that “Adding manpower to a late software project makes it later” (Brooks 25), which is something I have observed in small-scale settings. Several months ago, a large feature went into the main application I work on at my internship just a few days before the latest version was sent to systems integration and customer testing. Unfortunately, the complicated logic driving that feature was incorrect, but something about the feature made it unable to be removed from the branch we were using for the next release (I would explain why, but I was not involved in this issue). Many things went wrong in the creation of this feature, but as deadlines approached, our choices were limited, so two developers stepped in to help the original developer. The new developers, who were already acquainted with the larger system, still took more than a day to become familiar with the specifications of the feature. It took several more days to actually get the feature working. In the end, the release date was delayed by about a week. This isn’t much compared to the delays of some projects, but for my team of 9 developers who release new features and fixes every 12 weeks, this was a significant delay for something seemingly small.
Another interesting thing I noticed in this reading was the observation that programmers and project managers tend to be too optimistic about the time it takes to complete a project. I am certainly guilty of this. Over the summer, I took charge over a somewhat large UI refactor of an outdated portion of the application I work on at my internship. I originally estimated the project to be finished in November 2017, including unit testing. Now that it’s almost October 2017, and having experienced several complications, I realized I was probably too optimistic. Luckily, the project is a low-priority project, so the release date can be moved back. In the future, I know to plan for the fact that I, like many other software developers, am often too optimistic.
If there were an easier way to estimate time, and realize that we are often too optimistic, more projects might not fall behind schedule. But, as Brooks explains, this is one of the difficulties of project management that is difficult to overcome. If we underestimate how long a project will take to complete, then it will either be late, or be incomplete compared to the original vision. If we overestimate the time it takes to complete a project, the resulting product may be obsolete come time to release it. He did note, however, that projects tend to follow a set timeline better if at least half of the schedule is devoted to testing since we tend to be the most optimistic about testing and creating bug-free software.
The last—actually one of the first—things I noticed about Brooks’ book was how he consistently referred to programmers, project managers, and other professionals as men. In fact, the title is Mythical Man Month, in reference to the number of men assigned to a project. This didn’t hinder my ability to read and understand Brooks’ observations, but it was certainly distracting. In fact, his only reference to non-male people in chapters 1-4 was explaining that “the bearing of a child takes nine months, no matter how many women are assigned.” This was a good example for tasks that have sequential constraints, it was bothersome that the only mention of a non-male was in reference to a woman giving birth. While this reading assignment was a worthwhile read, I felt as though it was never talking about me or people like me, despite being a software developer. In this book, women are mothers who give birth, and men are programmers, managers, surgeons, etc. It felt as though it was specifically referencing male developers, further solidifying the stereotype that programmers, and professionals in general, are men.
6.4
Draw diagrams showing a conceptual view and a process view of the architectures of the following systems:
-
A ticket machine used by passengers at a railway stations.
-
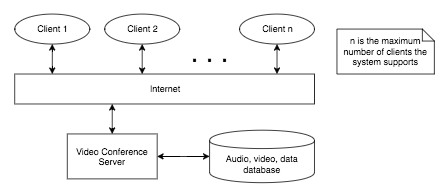
A computer-controlled video conferencing system that allows video, audio, and computer data to be visible to several participants at the same time.
-
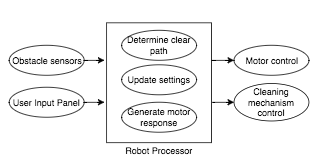
A robot floor-cleaner that is intended to clean relatively clear spaces such as corridors. The cleaner must be able to sense walls and other obstructions.
5.3
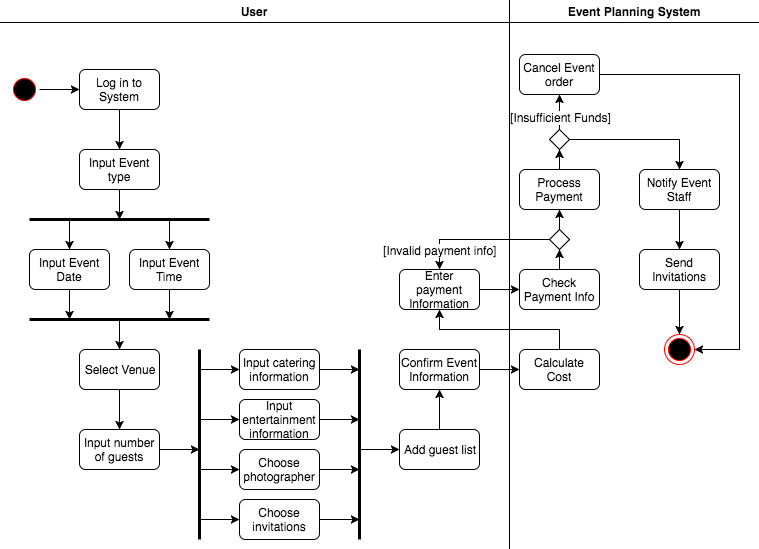
You have been asked to develop a system that will help with planning large-scale events and parties such as weddings, graduation celebrations, and birthday parties. Using an activity diagram, model the process context for such a system that shows the activities involved in planning a party (booking a venue, organizing invitations,,etc. ) and the system elements that might be used at each stage.
5.5
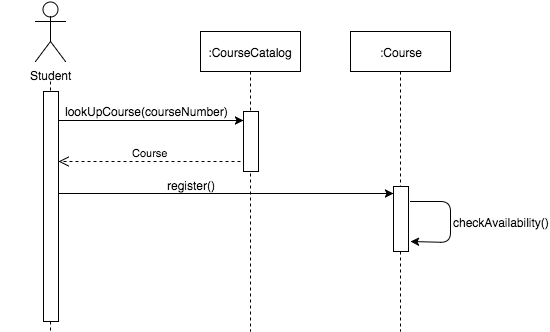
Develop a sequence diagram showing the interactions involved when a student registers for a course in a university. Courses may have limited enrollment, so the registration process must include checks that places are available. Assume that the student accesses an electronic course catalog to find out about available courses.
5.7
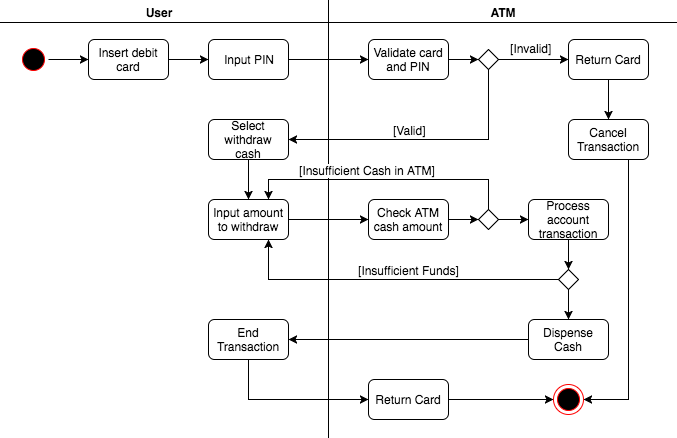
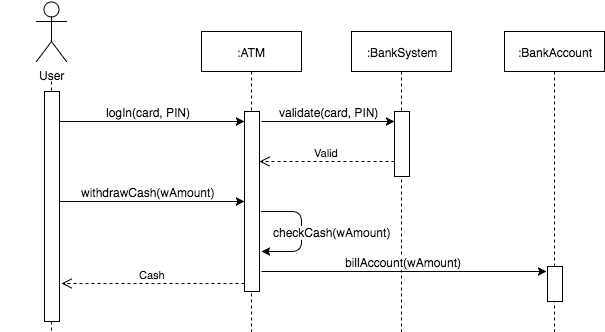
Based on your experience with a bank ATM, draw an activity diagram that models the data processing involved when a customer withdraws cash from the machine.
5.8
Draw a sequence diagram for the same system. Explain why you might want to develop both activity and sequence diagrams when modeling the behavior of a system.
It is important to include both activity and sequence diagrams when modeling the behavior of a system because activity diagrams model the flow of a use case and sequence diagrams model the interactions between objects in a use case. Each diagram offers a unique point of view to form a more accurate model of a certain behavior, reducing the number of misunderstandings between the client and developer.
In 11 Predictions for the Future of Frogramming, Peter Wayner discusses 11 ways the future of programming and technology will change or remain the same. Some of them I already predicted myself, such as the Internet of Things becoming much scarier regarding security, and others came as a surprise. I agreed with some of his predictions, and was skeptical of others. Regardless of anyone’s predictions, attempting to predict the future state of programming is a worthwhile effort. After all, no company wants to be behind another when more money can be made.
One of Wayner’s predictions that surprised me the most was that data will continue to be essential in our software. To me, this prediction seemed so obvious that it was hardly worth mentioning. Until we become all-knowing beings, data is the only way we can begin to know the state of something. Even when the best data analysts end up being wrong, like when nearly every poll predicted Clinton would win the 2016 presidential election turned out to be wrong, what else do we have? All we can do to make election predictions more accurate is to do something different with the data we have. Maybe we can represent it differently, sample it in a new way, or use different algorithms on it, but in the end, all of our software relies on data. Data isn’t going anywhere anytime soon, and programmers will need to continue to deal with it as software becomes more data-intensive.
Wayner also predicted that autonomous transportation is here to stay, and programmers will no longer decide what we, but where we go as well. In his prediction, Wayner pointed out a particularly disturbing aspect of autonomous transportation: advertising in the form of diverting our journey. While advertising a local restaurant is harmless in itself, changing my route every so often to drive past some business can create traffic nightmares and alarming privacy concerns. Current traffic apps such as Google’s Waze are already creating terrible traffic on neighborhood roads according to a 2016 Washington Post article. Autonomous transportation, such as self-driving cars, take all control away from their users. With a traffic app, a user can choose to ignore the directions presented to them, and go a different way. They could even go as far as turning off location services so no app can track their location. Self-driving cars, on the other hand, will likely always require location information to accurately navigate the car, and can take the user on whatever route it maps out, unless there is some sort of override feature. I have no doubt that autonomous transportation will become more prevalent in the future, however, I believe as software engineers we must tread carefully regarding traffic and privacy.
I noticed that many of Wayner’s predictions are based on the notion that the number of devices that run some sort of software will expand, and programmers will need to adapt to the fact that software development will most likely no longer revolve around PCs. In my home alone, I have at least six devices that can connect to the internet that are not a PC. My mother has even more than that, including a small home security system and an Amazon Alexa. From my point of view, it’s easy to see that PCs are no longer the centerpiece of personal technology. As software developers and engineers, we need to be adaptive to the rapid shift away from PCs alone to PCs and everything else that runs some sort of software and their implications regarding safety, security, privacy, the environment, and so on.
2.1
Suggest the most appropriate generic software process model that might be used as a basis for managing the development of the following systems. Explain your answer according to the type of system being developed:
-
A system to control antilock breaking in a car
In this case, the waterfall model is the most appropriate generic software process podel that might be used as a basis for development. A system that controls antilock breaking in a car is a safety-critical system, and issues related to safety can be expensive to correct during the implementation phase. The waterfall model requires all specifications and design documents to be complete before implementation, meaning they can be analyzed and safety problems are more likely to be avoided during implementation. Additionally, a system controlling antilock breaking in a car is a system that interfaces with hardware. Hardware, unlike sofware, is fairly inflexible, often making decisions on software functionality impossible during the implementation phase.
-
A virtual reality system to support software maintenance
A virtual reality system to support software maintenence would likely be implemented using software integration and implementation. Given that virtual reality is incredibly complex, and packages and frameworks for developing virtual reality software such as A-Frame, it seems the most appropriate to integrate an existing system into this new system.
-
A university accounting system that replaces an existing system
Without more details, it's hard to determine whether incremental development or the waterfall model would be most appropriate for this system. If this system is only implemented at one university, or the system is being replaced to reflect new accounting needs, then the incremental approach would be best because the system developers could get feedback during development and address the new needs that were not met by the previous system. However, if the new system were to be used by multiple universities or the system requirements for the new system were mostly identical, the waterfall approach might be better. The waterfall method works best when multiple institutions are involved in creating larger systems because it is easier to communicate system requirements.
-
An interactive travel planning system that helps users plan journeys with the lowest environmental impact
Incremental development would be the most appropriate software process model for this system. This system seems like its requirements could change at any point during or after the implementation phase. Users may request certain changes or new features, or specifications may change if a new environmental impact study were to be published. Therefore, the cost of making changes during and after the implementation phase need to be low.
Articles
Reflections
All of these articles, except the Wikipedia article on The Magical Number Seven, Plus or Minus Two, revolve around building safe, secure, and reliable software. In fact, the first recommendation for creating secure tire pressure monitoring systems in Security and Privacy Vulnerabilities of In-Car Wireless Networks was to follow basic reliable software design practices. They noted that impossible values were allowed to be displayed in the studied tire pressure monitoring systems. Had reliable software design practices been followed, some of the more obviously incorrect test cases could have been avoided. One possible reliable software design practices that could be used to design future tire pressure monitoring systems is test-driven development (TDD). The idea behind TDD is tests are written before development, and development is centered around tests, and tests must pass before development can continue. Ideally, the case where a valid tire pressure that also displays a tire pressure warning flag should have been caught before developing the system, and a test would have been written for that case in TDD.
Five years after Security and Privacy Vulnerabilities of In-Car Wireless Networks was published, the SPY Car Act was enacted. The SPY Car Act is essentially a federal regulation to ensure sensors and other computer systems in vehicles are secure. It even outlines a specific design principle to ensure vehicles remain safe in the event of an attack: “ISOLATION MEASURES.—The measures referred to in subparagraph (A) shall incorporate isolation measures to separate critical software systems from noncritical software systems.” This would ensure that if something like the tire pressure monitoring sensors were spoofed, the safety-critical systems in the car would retain their integrity. Ensuring a system is safe and secure also ties in with the notion of reliable systems. If a system is unsafe, or can easily be attacked, it has the potential to not function as specified, making it unreliable. Reliable systems must be able to fail gracefully, that way when the system is down for whatever reason, it causes as little trouble to its users as possible. Mike wood outlines multiple ways to handle failure in software systems in Preparing for the Future, and stresses that failure is not a matter of “if”, but “when.” After reading through each of the techniques, it became clear to me that regardless of what technique is implemented in a system to prevent or handle failure, those techniques are useless if the use case for the cause of failure was not foreseen. This is where, I believe, TDD is a useful software development practice for creating reliable software.
I also believe TDD supports the idea that humans have a hard time keeping more than seven—plus or minus two—objects in active memory at once. In TDD, you think of several test cases to develop code to pass those test cases, and repeat. This allows a developer to focus on test cases alone before worrying about the implementation of a system to pass those test cases. If we develop in a way that mirrors how much we can think about at one time, then the resulting system should be more reliable, safe, and secure.
4.5
Using the technique suggested here, where natural language descriptions are presented in a standard format, write plausible user requirements for the following functions:
- An unattended petrol (gas) pump system that includes a credit card reader. The customer swipes the card through the reader, then specifies the amount of fuel required. The fuel is delivered and the customer's account debited.
| Function: | Deliver fuel and debit customer’s account at an unattended gas pump. |
| Description: | Calculate the total cost of the amount of fuel specified by the customer, then dispense the specified amount of fuel and charge the customer’s account for the calculated cost. |
| Inputs: | Customer bank account information via credit card, amount of fuel required. |
| Outputs: | Amount of fuel required, bill to customer’s bank account. |
| Destination: | Customer’s bank account, customer’s car. |
| Action: | Compute the amount to charge the customer’s bank account by multiplying the amount of fuel required by the price of fuel (ensure the units for fuel and units in price per unit are identical), send bill to customer’s bank account using calculated cost and bank account information, then dispense the amount of fuel required. |
| Preconditions: | There must be room in the customer’s fuel tank for the required amount of fuel, funds for the amount of fuel required must be present in the customer’s account. |
| Postconditions: | Amount of fuel delivered was subtracted from the fuel station’s reservoir, customer’s account was charged correctly, the amount of fuel required was delivered. |
| Side Effects: | None. |
- The cash-dispensing function in a bank ATM.
| Function: | Dispense the correct amount of cash from an ATM. |
| Description: | Dispense the correct amount of cash inputted by a verified user. |
| Inputs: | Amount of cash required, bank account information via debit card, PIN number. |
| Outputs: | Amount of cash required |
| Destination: | User |
| Action: | Verify the user’s identity by matching the inputted PIN number to the bank account information from the inputted debit card. If the bank account information and PIN number combination is incorrect, stop the process and do not return any cash. If the bank account information and PIN number combination are verified, allow the user to input the amount of required cash by entering the number of each type of bank notes they want. Do not allow the user to input more cash than the ATM contains. Dispense the inputted amount of cash. |
| Preconditions: | ATM contains cash, user’s bank account must contain as much or more money than cash required. |
| Postconditions: | The amount of cash in the ATM decreased by the amount of required cash, the user’s bank account decreased by the amount of required cash, transaction is recorded in user’s bank account log. |
| Side Effects: | None. |
- In an internet banking system, a facility that allows customers to transfer funds from one account held with the bank to another account with the same bank.
| Function: | Transfers funds from one online account to another within the same bank. |
| Description: | A online banking service user transfers money from their account to the account of another user who uses the same bank. |
| Inputs: | Bank account information of the user who is transferring funds to another account via logging into banking service online, account number of other account to transfer funds into, amount of money to be transferred (W). |
| Outputs: | Confirmation sent to both accounts. |
| Destination: | Both bank accounts. |
| Action: | Determine which bank account to withdraw funds from using the bank account information supplied from the logged in user’s credentials (A1), determine where to send the withdrawn funds to using the account number supplied by the logged in user (A2), debit W from A1 and credit W to A2. |
| Preconditions: | The identity of A1 must be verified (must be logged in to online banking service), the inputted account number must be a valid bank account within the same bank, A1 must contain at least the amount of funds to be transferred. |
| Postconditions: | A1 had W fewer funds and A2 had W more funds. The sum of both accounts remained the same. |
| Side Effects: | None. |
4.6
Suggest how an engineer responsible for drawing up a system requirements speicification might keep track of the relationships between functional and non-functional requirements.
An engineer could determine the functional and non-functional requirements of a system before developing a system, then write out the requirements in such a way that closely related functional and non-functional requirements are visually closer together, or draw lines to closely related requirements. Similar to modelling classes in UML, being able to have a visual representation of the relationships between functional and non-functional requirements allows the engineer to have a better grasp of their relationships.
4.7
Using your knowledge of how an ATM is used, develop a set of use cases that could serve as a basis for understanding the requirements for an ATM system.
- Use Case: Deposit cash and checks:
- Primary Actor: Owner of a bank account
- User inputs their bank account and PIN number.
- If their credentials are correct, allow them to deposit cash and checks together.
- Credit the user for the amount of cash and amount specified on the checks.
- If the credentials are incorrect, do not allow money to be deposited.
- Use Case: Withdraw cash:
- Primary Actor: Owner of a bank account
- User inputs their bank account and PIN number.
- If their credentials are correct, allow them to enter the amount of cash they wish to withdraw.
- If their account contains at least the amount of specified cash, withdraw the amount of cash specified from the user’s account. If not, do not output any cash.
- If the credentials are incorrect, do not allow money to be withdrawn.
- Use Case: User does nothing:
- Primary Actor: Owner of a bank account
- User inputs their credentials correctly and does not choose an action.
- User is logged out after 60 seconds of inactivity.
- Use Case: Load Cash into ATM:
- Primary Actor: ATM Maintenance Worker
- Maintenance worker enters maintenance mode with admin credentials.
- Maintenance worker selects option to load cash.
- Maintenance worker loads cash into ATM.
- ATM counts cash loaded, verifies amount is correct to Maintenance Worker.
- If cash count is incorrect, return cash, repeat process.
Articles
Reflections
Each of the above readings revolve around a series of detrimental software failures or potential software failures due to a multitude of improper software engineering practices. Some of the incidents, such as the accidents described in The Role of Software in Spacecraft Accidents were financially costly, whereas others, such as the Therac-25 accidents, cost some patients their lives. To me, it is obvious that ethical software systems should never cause financial or physical harm to anyone or any environment. Yet, it seems to be far too common. As I read these articles, I wondered how these issues slipped through the cracks during development, and how could they have been prevented.
Leveson described the most common reasons for security and safety failures best: tight budgets, poor communication, unnecessary software complexities, reused code assumed to be safe, poor or missing specifications, poor engineering standards and practices, etc. One of the most upsetting things to read as a software engineer — and most frightening as a consumer — is that when budgets are slim, “the first things to be cut are often system safety, system engineering, mission assurance, and operations, which are assigned a low priority and assumed to be the least critical parts of the project” (Leveson 5). What’s worse, is that one a system has proven itself successful, the engineers of its descendant systems tend to assume that the new systems will function safely and securely as well. For example, the Mars Climate Orbiter used a navigation system that worked well for over 30 years, so the focus of the project was shifted to meeting budgets and deadlines instead of mission risk. Additionally, the Therac-25 radiation therapy machine failed on multiple occasions due to a software system that was assumed to be safe due to the success of the Therac-20. The assumption was misguided however, because the same software flaw was present in the Therac-20, except the Therac-20 never harmed any patients because it featured hardware safety checks that were falsely deemed unnecessary in the Therac-25. In order to avoid issues like these in the future, systems must be checked for safety, regardless of how much of that system was repurposed from an older system. In fact, for safety-critical and security-critical systems, it might be safer and more secure to rewrite new software to avoid overconfidence in a new system.
Another point that caught my interest, was the following statement from our textbook regarding security challenges on page 368: “When considering safety, you can assume that the environment in which the system is installed is not hostile. No one is trying to cause a safety-related incident.” I found this to be relevant to the FBI’s warning about modern vehicles becoming increasingly vulnerable to remote exploits. Before cars commonly featured USB ports, diagnostics ports, Bluetooth, or Wi-Fi, the main concern when designing a car was safety, and it remains the most important aspect of vehicle design today. However, as vehicles become more reliant on software, and more connections to that software are introduced, security becomes another major concern in an industry that hardly focused on security in the past. As I read the public service announcement from the FBI, I wondered if vehicle manufacturers were slow to address security concerns because it has never been an issue before. Maybe, those manufacturers assumed that, like safety concerns, nobody would deliberately attempt to hack into a car. After all, security concerns in vehicles are sometimes safety concerns as well if the attacker can gain access to the vehicle’s steering or brakes in transit. Now that the FBI has brought those concerns to light, hopefully manufacturers will begin to address those concerns as well.
11.4
What is the common characteristic of all architectural styles that are geared to supporting software fault tolerance?
Redundancy and Diversity are the most common characteristics among architectural systems that support fault tolerance. The idea is that if one of the systems in place to prevent system failure fails, then there will be at least one other, slightly different protection in place to keep the system running.
11.7
It has been suggested that the control software for a radiation therapy machine, used to treat patients with cancer, should be implemented using N-version programming. Comment on whether or not you think this is a good suggestion.
N-version programming will likely be the safest implementation of software to control a radiation therapy machine. Similar to the software systems that control aircraft and nuclear reactors, if the software for a radiation therapy machine were to fail, lives could be lost. Although I believe that N-version programming is a good way to implement software for a radiation therapy machine, relying on software alone in a system that can easily kill a person is a terrible idea. A radiation therapy machine must have hardware safety checks in addition to software safety checks. For instance, a software issue in the Therac-25 radiation therapy machine was directly related to the deaths of more than one person. The software issue present in the Therac-25 was also found in the Therac-20, an older model, but the Therac-20 never caused any physical injury. This was because the Therac-20 had hardware safety checks so that when a signal for a massive dose of radiation was sent from the software to the hardware, certain fuses and breakers would be tripped, preventing a patient from receiving a potentially fatal radiation overdose.
11.9
Explain why you should explicitly handle all exceptions in a system that is intended to have a high level of availability.
As the number of unhandled exceptions increase, the probability that one of those unhandled exceptions will be encountered during runtime increases. Availability is defined as the probability that a system, at a point in time, will be operational and able to deliver the requested services. This means that if the probability of encountering an unchecked exception is high, so is the probability that a system will not be operational at a given time. Therefore, in order to have a highly available system, all exceptions must be explicitly handled.
12.5
A train protection system automatically applies the brakes of a train if the speed limit for a segment of track is exceeded, or if the train enters a track segment that is currently signaled with a red light (i.e., the segment should not be entered). There are two critical-safety requirements for this train protection system:
- The train shall not enter a segment of track that is signaled with a red light.
- The train shall not exceed the specified speed limit for a section of track.
Assuming that the signal status and the speed limit for the track segment are transmitted to on-board software on the train before it enters the track segment, propose five possible functional system requirements for the onboard software that may be generated from its system safety requirements.
- If the speed limit of the upcoming segment of track is lower than the current speed of the train and the signal is green, gradually apply the brakes until the new speed limit is reached.
- If the speed limit of the upcoming segment of track is higher than the current speed of the train and the signal is green, gradually accelerate until the new speed limit is reached.
- If the upcoming segment of track is signaled with a red light, begin applying the brakes so that the train can safely stop at the signal.
- If the signal status changes from red to green while slowing down to approach the signal and the train is currently moving faster than the upcoming speed limit, continue gradually slowing down to match the speed limit of the upcoming speed limit.
- If the signal status changes from red to green while slowing down to approach the signal and the train is currently moving slower than the upcoming speed limit, gradually speed up to match the speed limit of the upcoming speed limit.
10.6
Explain why it is reasonable to assume that the use of dependable processes will lead to the creation of dependable software.
Software that was created using dependable software processes means that the software was created using standardized and robust techniques, and redundant and diverse validation and verification. Dependable processes are also auditable, meaning that people not a part of the process can understand the process as well, so that others can verify that standards were enforced during software development. Also, dependable processes are documentable so that the process documents what activities are to be in the process, and documentation is made during those activities.
Assuming that software created using dependable processes is similar to assuming that a building is dependable if it was created using dependable processes. We generally determine whether or not buildings are safe if they were built using dependable materials, the building was built to meet certain codes, and the builders used proper construction techniques. Software is created using much different processes, but if those processes are dependable, then the software should also be dependable.
10.10
It has been suggested that the need for regulation inhibits innovation and that regulators force the use of older methods of systems development that have been used on other systems. Discuss whether or not you think this is true and the desirability of regulators imposing their views on what methods should be used.
Innovation in software requires regulation. Creating software, unlike solving physical science problems, is bound only to a set of requirements made up by humans. Creating software to do something new is possible, but if that software is not dependable, then I believe that the software is not truly an innovative piece of software. Sure, the software may introduce a novel concept, but if it’s not dependable, then the software can cause frustration, economic loss, or physical damage. Solutions that can introduce more problems, are often not solutions at all, and therefore not innovative.
Though they may feel restricting at times, regulations are often in the best interests of creating dependable software, and generally desirable. However, not all regulations may be desireable. Our ideas of right and wrong change, and our standards of safety change as we learn more about health and the environment around us. In order for a regulation to be desirable, it must be periodically revisited in order to reflect the most recent standards for health, safety, ethics, environmental impact, etc. Out of date regulations can be detrimental to our society because they allow for potentially unsafe software to be in use.
Software development may often seems simple and straightforward. At the very least, it may seem as though software engineers have a decent idea of the costs of developing some software system. However, as Frederick Brooks notes in No Silver Bullet: Essence and Accidents of Software Engineering, it can quickly become a business nightmare. Unfortunately, the nature of software means that it will likely never have drastic reductions in development costs from a single advancement in technique or technology. Brooks explains how software is inherently complex because ideal software should not include repeated implementation (think DRY: Don’t Repeat Yourself, make a subroutine that can be called more than once). Additionally, software revolves around arbitrary human constructs that are subject to constant change rather than nature. Plus, software is invisible, and intangible, making it more difficult to visualize and understand. Brooks also outlines several potential “silver bullets” to make software engineering more efficient, but given that he wrote No Silver Bullet in the 1980’s, I believe examining current working software engineering solutions alongside Brook’s speculations is worthwhile.
When I think about massive software projects with daunting software engineering problems, the first company that comes to mind is Google. According to Why Google Stores Billions of Lines of Code in a Single Repository by Rachel Potvin and Josh Levenberg, 95% of the software used by its developers worldwide is stored in a single repository. At first, it sounded insane that a company with so many applications and thousands of developers working on those applications across the globe are all committing code to one massive repository. But, Google couldn’t become the giant that they are today if their developers spent most of their time sorting through thousands of merge conflicts. Google has mastered time-sharing, but not in the sense that Brooks described. Brooks claimed that in the time it takes to compile and execute a program, a developer can forget what they were working on. Therefore, as technology got better, it would take less time to compile a program, meaning developers would remember where they left off, which increases productivity. Even though nearly every program can be compiled virtually instantaneously today, time-sharing is still something to continue perfecting. As applications get larger, and more and more developers are assigned to work in a single repository, a single developer’s code base may be several commits behind the current version. Today, a developer may not forget what they were working on in the time it took to compile their code, but the application they were working on may have changed while they were working. Software such as Git and Subversion have made it possible for developers to work on a single repository at the same time, but it’s not flawless.
For instance, in Kode Vicious, a reader asked George Neville-Neil when they should give up cherry-picking changes into a branch and merge. Neville-Neil responded by saying that most developers end up in nightmarish cherry-picking situations because they rarely merge whatever code they are working against into their own code. Therefore, for moderately sized repositories, the issue of being far behind a remote code base can be fixed by getting in the habit of merging often. However, Google’s repository is far from moderately sized. Even a developer with perfect merging habits could be far behind the latest version with each commit due to the sheer size and scope of Google’s repository. Google overcame this issue by using trunk-based development coupled with high programming standards. Trunk-based development is where all developers commit to a single trunk, which is similar to the master branch in git. There are no long-running branches, meaning fewer conflicts because there is only one true code base and no confusion over which branch to merge into a local branch and vice versa. Google also implements automatic testing before a commit is merged and enforces strict code review so that bad changes are unlikely to be merged into the trunk.
In my opinion, the most interesting about Google’s time-sharing advancement, trunk-based development using Piper and CitC, is that it is still no “silver bullet” for Google’s massive repository. It’s simply a better engineering solution compared to what was available decades ago. The cost to maintain code integrity is high in trunk-based development compared to branch-based development. Also, Google has to control permissions on files that could be damaging to their repository, such as certain configuration files, making open source contributions difficult in their trunk-based development environment. In fact, Google’s Android and Chrome teams use Git versioning and are not a part of Google’s massive repository because open source collaborations are essential to those applications. Despite impressive innovations in software engineering since the time No Silver Bullet was written, it seems as though Brooks’ claim that there will never be a “silver bullet” has yet to be disproven 30 years later.
1.3
What are the four important attributes that all professional software should have? Suggest four other attributes that may sometimes be significant.
The four attributes that all professional software should have are acceptability, dependability and security, efficiency, and maintainability:
- Software that is acceptable must be acceptable to the type of users for which it is designed. This means that it must be understandable, usable and compatible with other systems that they use.
- Dependable and secure software is software that is reliable, safe, secure, etc. Dependable software should not cause physical or economic damage if it fails. It should also be secure so that malicious software cannot access or damage the system.
- Efficient software Software should not make wasteful use of system resources such as memory and processor cycles. Efficiency therefore includes responsiveness, processing time, resource utilisation, etc.
- Maintainable software is written in such a way that it can adapt to the changing needs of customers.
Four other suggestions that might be important are:
- Accessibility: software should be accessible to its users who may have some sort of physical disability. It should also not seem excessively complicated to its users. This may not be applicable to all software systems, but it should always be a consideration.
- Portability: Software should be usable on more than one operating system, web browser, etc. unless intended for a specific purpose on a specific system.
- Documentation: Software should be sufficiently documented so that users can troubleshoot errors and determine how to use the software, and developers can properly implement and maintain the software. This is important to create maintainable software.
- Mobile Compatibility: Since smartphones are the only way some people can access the internet, web applications should consider mobile browsers during development, especially if the application is used by a wide variety of users.
1.8
Discuss whether professional engineers should be licensed in the same way as doctors or lawyers.
Professional engineers should be licensed similar to doctors and lawyers, especially if they are working on large, widely used systems, or systems that could cause damage during failure. Unlicensed engineers could oversee systems without regard to certain areas of study, such as cybersecurity or computing ethics. A licensed would ensure that the engineer is proficient in each common area of study, regardless of education background.
1.9
For each of the clauses in the ACM/IEEE Code of Ethics shown in Figure 1.4, propose an appropriate example that illustrates that clause
- Public: Software engineers should not develop code that gives out personal user information without permission.
- Client: Software engineers should not have special access to software data for personal gain. A more specific example of this would be an engineer should not be able to temporarily alter product prices an online shopping system for personal discounts.
- Product: Software engineers should not skip any consumer requirements because they may be difficult to maintain.
- Judgement: Software engineers should not take credit for another engineer's work. They should also be able to contribute to the system they are working on, not just be present in meetings.
- Management: Management should ensure that software developers are ethically developing a system. A software engineer should hold all developers to the highest possible standard.
- Profession: A software engineer must keep up with ethical issues, advances in technology, changing business environments, and they must be able to work in these changing environments without sacrificing integrity.
- Colleagues: Software engineers should treat all colleagues as capable, and intelligent people. Biases must be avoided.
- Self: A software engineer should not stop learning once they get their degree.
1.10
To help counter terrorism, many countries are planning or have developed computer systems that track large numbers of their citizens and their actions. Clearly this has privacy implications. Discuss the ethics of working on the development of this type of system.
This is a case of sacrificing some liberty for the sake of safety. Generally, mass invasion of privacy should be avoided, therefore before development of this project takes place, the benefits should be analyzed. Additionally, how the system tracks citizens' actions is an important consideration. If the system solely tracks the actions of citizens of Middle-Eastern descent, or who practice Islam, then the system is inherently discriminatory. Discriminatory systems should always be avoided, as they only worsen socioeconomic issues.
My name is Samantha Word, but I generally go by Sam. I am a senior at College of Charleston majoring in Computer Science with a minor in Mathematics and Astronomy.
I am currently a Ruby on Rails developer for MUSC. The primary application that my teammates and I work on is SPARCRequest. SPARCRequest is an open source application used by multiple unstitutions across the US. It is best described by our README:
SPARC (Services, Pricing, and Applications for Research Center) is a web based research management system that integrates research and clinical care workflows with a focus on service request catalog, billing compliance, proposal and budget development, work fulfillment data collection, invoicing and billing, and impact data through grants and publication associations.
When I am not studying or working, I love to cook. I find cooking to be immensely rewarding, especially when I perfect a recipe made from scratch. It's just as rewarding as creating a piece of software, and it provides a meaningful break from technology. Someday, I would like to be a Software Developer or Engineer with a garden full of fresh vegetables.
 A screenshot of our test suite
A screenshot of our test suite